Installing Let's Encrypt Wildcard SSL for Ubuntu, Debian and Hestia CP
SSL Certificate Installation Guide
Let's Encrypt is a non-profit certificate authority that provides free X.509 certificates for TLS encryption through an automated process designed to replace the current complex process of manually creating, verifying, signing, installing and updating certificates for secure websites. Let's Encrypt recently introduced a Wildcard certificate for your domain, now you can use ssl without wildcards for your domain and for multiple subdomains with just one SSL certificate.
This guide will work with Linux distributions such as CentOS, Ubuntu, Debian. Installation is done using Ubuntu OS as an example, to install git on CentOS OS, you need to use package managers yum, instead of apt-get.
- Install the acme.sh script:
cd /root
sudo apt-get install socat git
git clone https://github.com/Neilpang/acme.sh.git
cd ./acme.sh
./acme.sh --install
After installation, a cron job will be created for automatic certificate renewal. You can check if the job was added by running the command:
crontab -l
Before issuing a certificate, set Let's Encrypt as the default certification authority:
bash ./acme.sh --set-default-ca --server letsencrypt
- Requesting a release:
bash acme.sh --issue -d testfrnx.ru -d *.testfrnx.ru --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
Instead of testfrnx.ru you must specify your domain.
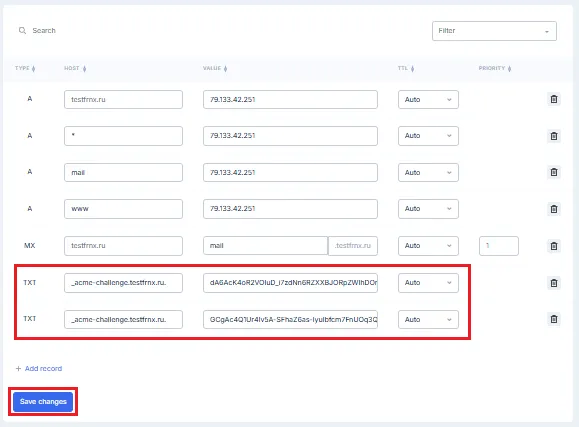
- The script will generate 2 TXT records to be added to DNS panel:
[Tue Jun 8 14:23:11 MSK 2021] Domain: '_acme-challenge.testfrnx.ru'
[Tue Jun 8 14:23:11 MSK 2021] TXT value: 'GCgAc4Q1Ur4Iv5A-SFhaZ6as-IyuIbfcm7FnUq3Qxs'
...
[Tue Jun 8 14:23:12 MSK 2021] Domain: '_acme-challenge.testfrnx.ru'
[Tue Jun 8 14:23:12 MSK 2021] TXT value: 'dA6AcK4oR2VOIuD_i7zdNn6RZXXBJORpZWlhDOmk96A'
When adding a record, you should add a period at the end of the record name. For example:
TXT record _acme-challenge.testfrnx.ru.
value : "dA6AcK4oR2VOIuD_i7zdNn6RZXXBJORpZWlhDOmk96A"
TXT record _acme-challenge.testfrnx.ru.
value : "GCgAc4Q1Ur4Iv5A-SFhaZ6as-IyuIbfcm7FnUOq3Qxs"
- Checking to see if the DNS records have been updated
dig txt +short _acme-challenge.testfrnx.ru
"GCgAc4Q1Ur4Iv5A-SFhaZ6as-IyuIbfcm7FnUOq3Qxs"
"dA6AcK4oR2VOIuD_i7zdNn6RZZXXBJORpZWlhDOmk96A"
- After updating the DNS, resume issuing the certificate:
bash acme.sh --renew -d testfrnx.ru -d *.testfrnx.ru --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
[Tue Jun 8 15:26:45 MSK 2021] Renew: 'testfrnx.ru'
[Tue Jun 8 15:26:46 MSK 2021] Using CA: https://acme-v02.api.letsencrypt.org/directory
[Tue Jun 8 15:26:46 MSK 2021] Multi domain='DNS:testfrnx.ru,DNS:*.testfrnx.ru'
[Tue Jun 8 15:26:46 MSK 2021] Getting domain auth token for each domain
[Tue Jun 8 15:26:46 MSK 2021] Verifying: testfrnx.ru
[Tue Jun 8 15:26:50 MSK 2021] Success
[Tue Jun 8 15:26:50 MSK 2021] Verifying: *.testfrnx.ru
[Tue Jun 8 15:26:54 MSK 2021] Success
[Tue Jun 8 15:26:54 MSK 2021] Verify finished, start to sign.
[Tue Jun 8 15:26:54 MSK 2021] Lets finalize the order.
[Tue Jun 8 15:26:54 MSK 2021] Le_OrderFinalize='https://acme-v02.api.letsencrypt.org/acme/finalize/126277849/10255533047'
[Tue Jun 8 15:26:55 MSK 2021] Downloading cert.
[Tue Jun 8 15:26:55 MSK 2021] Le_LinkCert='https://acme-v02.api.letsencrypt.org/acme/cert/03b7103ef19e6ed4f7ed37a88639dfc16fda'
[Tue Jun 8 15:26:56 MSK 2021] Cert success.
-----BEGIN CERTIFICATE-----
MIIFKzCCBBOgAwIBAgISA7cQPvGebtT37TeohjnfwW/aMA0GCSqGSIb3DQEBCwUA
MDIxCzAJBgNVBAYTAlVTMTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQD
EwJSMzAeFw0yMTA2MDgxMTI2NTVaFw0yMTA5MDYxMTI2NTVaMBYxFDASBgNVBAMT
C3Rlc3Rmcm54LnJ1MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0CVy
hiWdP/ctjDvgdrtpqj7TWhonFK/0Kyp/EHh5QyjU/9eqh/3XzeLN404Qw1wzWA2M
3PUMUtWHaWoQNL97cWT493BkC8VmfLIFCdxWl8YPQpFg1ue6P+ELveYZKZQdOJ9e
jviO/LKv8IioXboLoI2BmtA8aDV1A/bUKPces3jAVdOD/YKRGbyHY0rcqsJotmC4
Uf5qRmPpxM9Vz9QwSTsj5/XlSQgJsX4VTozoU2i4bjH54mQYqr2t4lsklCsJx0BR
IofOYG3mYoWTdJFSq6aufzOIIax46KZItcGoxbB/xOvLTMancJrHgutyvWFcMHod
3wUjjqoxMM3zLJuaOwIDAQABo4ICVTCCAlEwDgYDVR0PAQH/BAQDAgWgMB0GA1Ud
JQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAMBgNVHRMBAf8EAjAAMB0GA1UdDgQW
BBQ13H1ptA55SgCPtLPn7WPw5dNzfjAfBgNVHSMEGDAWgBQULrMXt1hWy65QCUDm
H6+dixTCxjBVBggrBgEFBQcBAQQRJMEcwIQYIKwYBBQUHMAGGFWh0dHA6Ly9yMy5v
LmxlbmNyLm9yZzAiBggrBgEFBQcwAoYWaHR0cDovL3IzLmkubGVuY3Iub3JnLzAl
OMRYIhVy2z1EAP/fPNiSPQ6v2wB2AG9Tdqwx8DEZ2JkApFEV/3cVHBHZAsEAKQaN
sgiaN9kTAAABeeuXDPkAAQDAEcwRQIhAL0fmCcsEIIB7BZuX1fy0Y7c6XkaoaE2
MmWcI75fbQV6AiA+gD9kPSX5WFu0aCRSRj2cBnyDzr/WBUvw/xLQ3UF2bzANBgkq
hkiG9w0BAQsFAAOCAQEAIfPpNQGil4ebxGfv6yGK8bXzg7nHnUx7PQ//Bsz47OXt
fC5URvam9+8lhzRycD5RCJbzhvW8kqNEx6xOavsMlnpkVfiQYqVCTPxGitsw4ETF
iYHT6s1xCLqqek/QI9oy+A0QIdmaI3tEMiDmtK5pbnATWlmKUP6eUErZZTuaioE4m
vTYOXId0nrMeZSa/N62mSJfpuQBfk3K1xiYVGxci6WwbB4PmfZX+hOQNAFn+zoWQ
Rl3kO4CDbCxsaXCzxz1BW65arox2vkAlXVHznLxzTBRa5ysJi6U6xWGg8VpUsPwF
1O/2l90+LYCsQ9Ib+SbsoD1TTkW6l/sKotVE43GTZQ==
-----END CERTIFICATE-----
[Tue Jun 8 15:26:56 MSK 2021] Your cert is in /root/.acme.sh/testfrnx.ru/testfrnx.ru.cer
[Tue Jun 8 15:26:56 MSK 2021] Your cert key is in /root/.acme.sh/testfrnx.ru/testfrnx.ru.key
[Tue Jun 8 15:26:56 MSK 2021] The intermediate CA cert is in /root/.acme.sh/testfrnx.ru/ca.cer
[Tue Jun 8 15:26:56 MSK 2021] And the full chain certs is there: /root/.acme.sh/testfrnx.ru/fullchain.cer
After issuing the certificates, they need to be added to the domain.
To enable Hestia CP to add the certificates, rename them using the following commands:
mv /root/.acme.sh/testfrnx.ru_ecc/ca.cer /root/.acme.sh/testfrnx.ru_ecc/testfrnx.ru.ca
mv /root/.acme.sh/testfrnx.ru_ecc/fullchain.cer /root/.acme.sh/testfrnx.ru_ecc/testfrnx.ru.crt
Replace testfrnx.ru with your domain name.
- Add the issued certificates to the domain:
v-add-web-domain-ssl USER testfrnx.ru /root/.acme.sh/testfrnx.ru_ecc/
Where:
-
USER— the user who owns the domain, -
testfrnx.ru— your domain, -
/root/.acme.sh/testfrnx.ru_ecc/— the path to the certificates.
"If a certificate was already installed for the domain, update it with the new one:"
v-update-web-domain-ssl USER testfrnx.ru /root/.acme.sh/testfrnx.ru_ecc/
Adding a Wildcard SSL Certificate for a Subdomain
- Copy the domain's Wildcard SSL certificate:
cp /home/USER/conf/web/testfrnx.ru/ssl/testfrnx.ru.ca /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.ca
cp /home/USER/conf/web/testfrnx.ru/ssl/testfrnx.ru.crt /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.crt
cp /home/USER/conf/web/testfrnx.ru/ssl/testfrnx.ru.key /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.key
- Add the certificates to the subdomain using the command:
v-add-web-domain-ssl USER sub.testfrnx.ru /home/USER/conf/web/testfrnx.ru/ssl/
- Remove the previously copied certificates:
rm /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.ca
rm /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.crt
rm /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.key
To update the certificates you need to run this command after 90 days, update the TXT dns record as below:
acme.sh --issue -d testfrnx.ru -d *.testfrnx.ru --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
Where testfrnx.ru is your domain name.

Automatically update let's encrypt certs with a Cron job, add this daily cron to check auto-update:
0 0 * * * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null
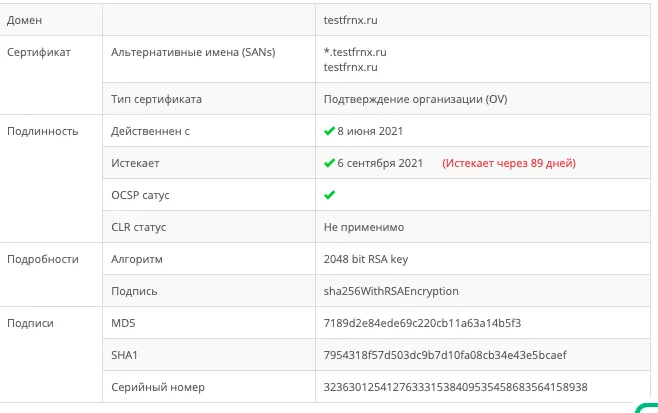
You can check if the certificate is installed correctly using this [service] (https://www.leaderssl.ru/tools/ssl_checker).
Help
If you encounter any difficulties or need assistance, please create a request to our support team through the ticket system, and we will be happy to help you.