Let's Encrypt certificate issue on older devices
30 Sep 2021 14:01:15 GMT IdenTrust DST Root CA X3 Root Certificate expired
Let's Encrypt is a non-profit certificate authority that provides free X.509 certificates for TLS encryption through an automated process designed to replace the current complex process of manually creating, verifying, signing, installing and updating certificates for secure Web sites.
As a result of the expiration of the DST Root CA X3 root certificate, outdated devices that have not received updates for a long time and do not support the new ISRG Root X1 root certificate, no longer trust the old certificate and when visiting sites that use certificates from Let's Encrypt, they give warnings or cannot establish a secure connection.
Obsolete devices and OS are older than 5 years, including:
- Windows XP up to SP3 (as well as for SP3 and Windows 7, if the root certificates were not automatically renewed).
- macOS before 10.12.1.
- iOS up to 10.
- Android up to 2.3.6 (at the same time, access to services may still be due to the peculiarities of verifying root certificates, and versions up to 7.1.1 will no longer support the certificate in 2024).
- Ubuntu before 16.04.
- Debian before 8.
- Sony PlayStation 3 and 4 with firmware up to 5.00.
- Older smart TVs and smart home devices.
- Devices using OpenSSL version 1.0.x.
The best solution would be to update the software to the latest versions, which already include support for the new root certificate. It is worth taking measures to solve the problem only if it is necessary, for example, a fairly large part of the service audience uses outdated software and they are critical for the project.
From the client's side, you can:
- Manually install the ISRG Root X1 root certificate if it is not present in the storage of the system or software used.
- Remove obsolete DST Root CA X3 certificate. Having an outdated root certificate can interfere with the normal operation of services that use Let's Encrypt certificates.
Warning! It is not possible to solve the problem in this way on all devices.
Windows 7 In the OS Windows 7, the root certificate chain had to be updated if operating system updates are enabled, otherwise the root certificate must be installed on your own by following these steps:
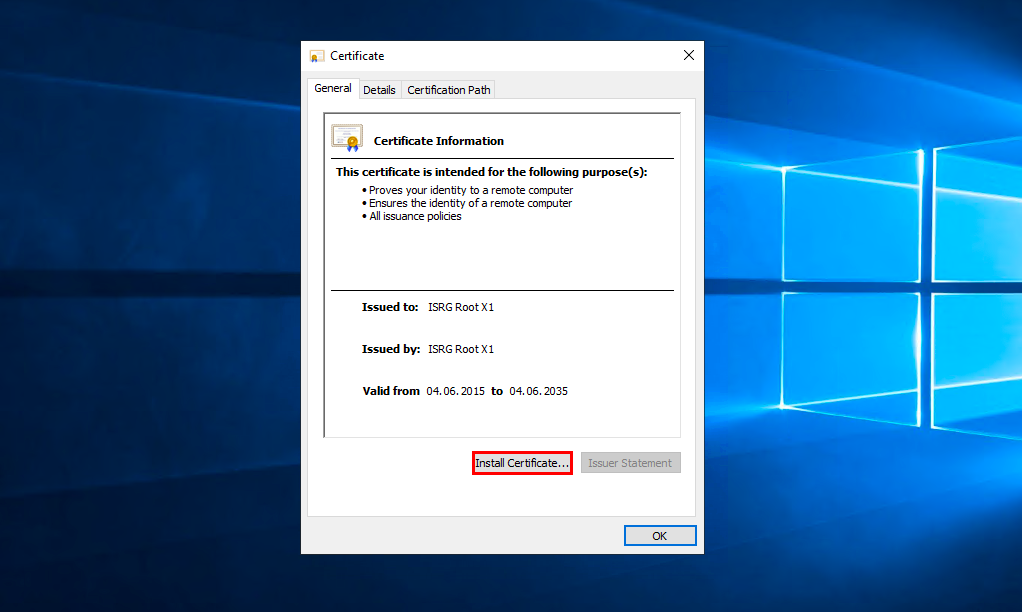
Download root certificate ISRG Root X1 with site Let's Encrypt format der. Run the downloaded file and allow it to open by clicking Open. In the window that appears, click Install Certificate:
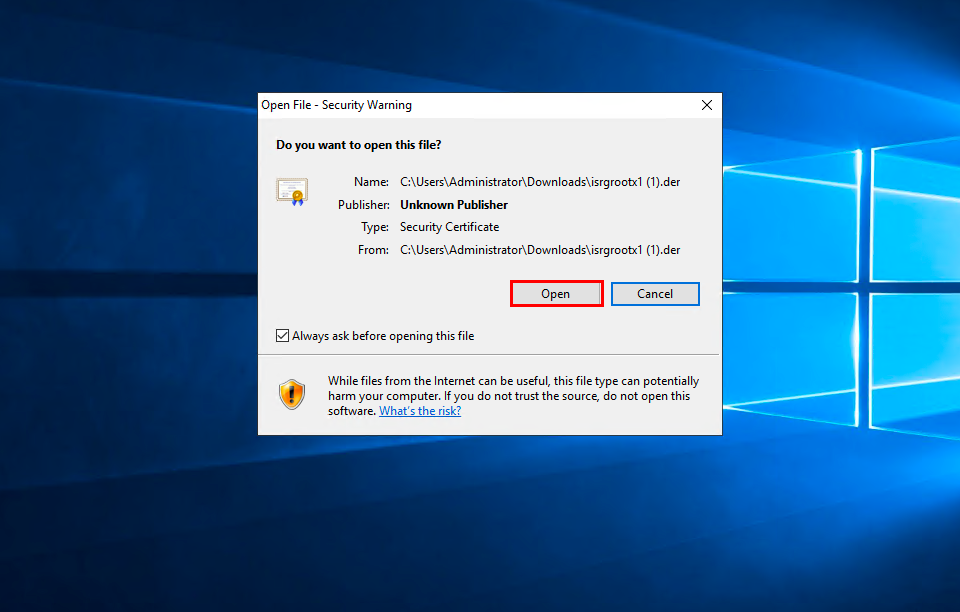
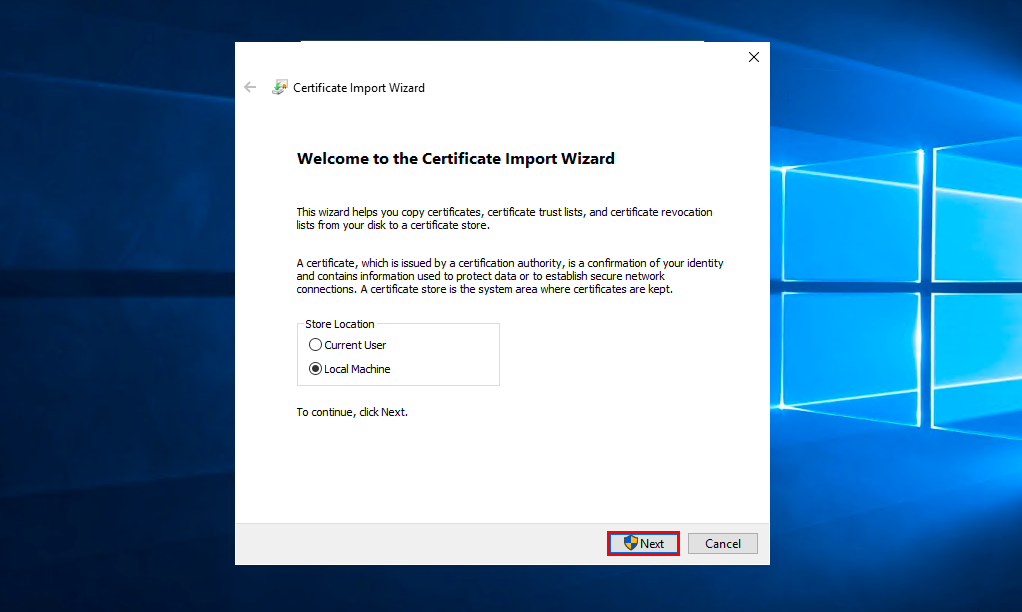
Select who you want to install the certificate for and click Next. Select item Place all certificates in the following store and press Browse:
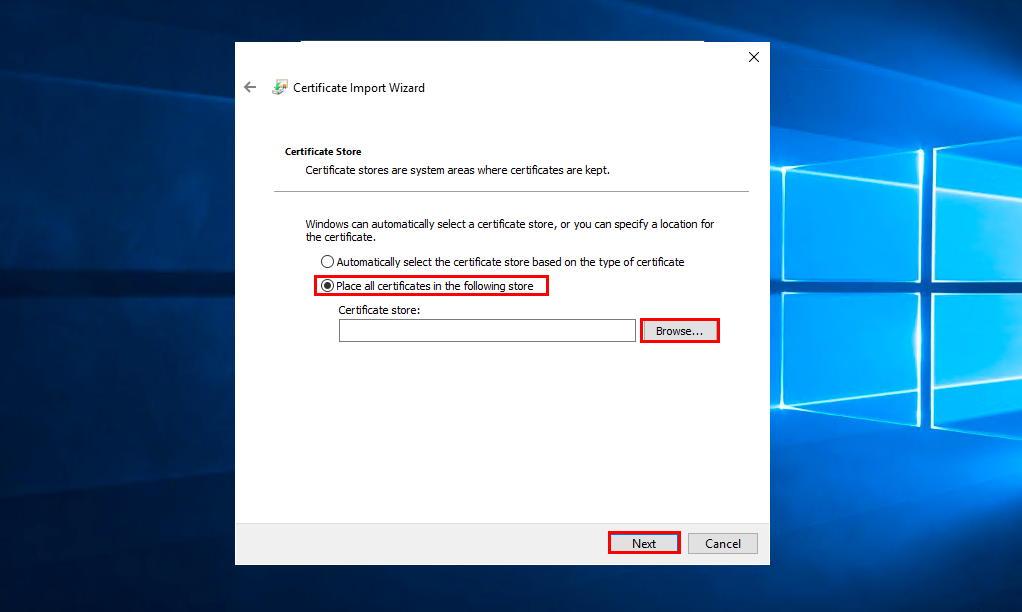
Select storage Trusted Root Certification Authorities and press OK:
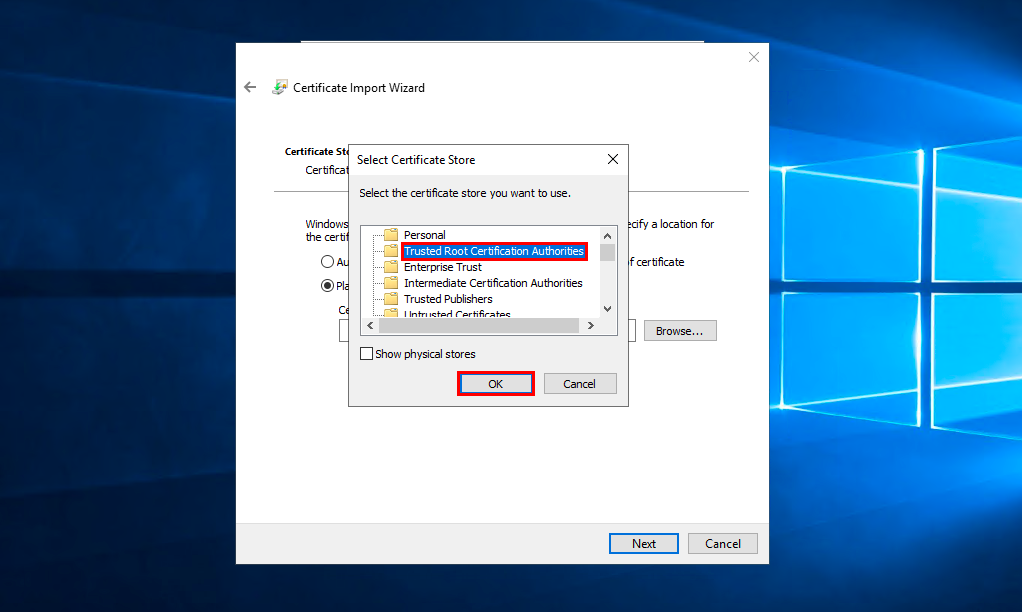
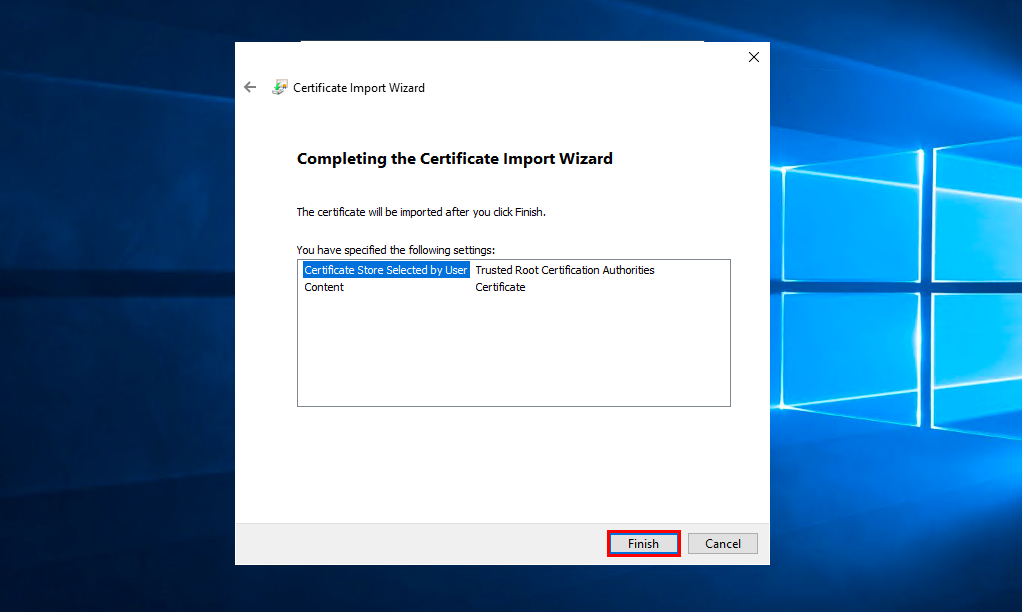
Clickon Next, check the correctness of the selected data and click Finish.
Debian/Ubuntu
- To check if the root certificate is in the trusted list, run the command in the terminal:
awk -v cmd='openssl x509 -noout -subject' ' /BEGIN/{close(cmd)};{print | cmd}' < /etc/ssl/certs/ca-certificates.crt | grep "ISRG Root X1"
- If the command output will show subject=C = US, O = Internet Security Research Group, CN = ISRG Root X1, then no further action is necessary, if not, then run the command.
curl -k https://letsencrypt.org/certs/isrgrootx1.pem.txt | sudo tee /usr/share/ca-certificates/mozilla/ISRG_Root_X1.crt ; sudo echo "mozilla/ISRG_Root_X1.crt" >> /etc/ca-certificates.conf ; sudo update-ca-certificates
Check the operation of the services with which access problems occurred.
CentOS
- To check if the root certificate is in the trusted list, run the command in the terminal:
awk -v cmd='openssl x509 -noout -subject' ' /BEGIN/{close(cmd)};{print | cmd}' < /etc/ssl/certs/ca-bundle.crt | grep "ISRG Root X1"
- If the command output will show subject=C = US, O = Internet Security Research Group, CN = ISRG Root X1, then no further action is necessary, if not, then run the command.
trust dump --filter "pkcs11:id=%c4%a7%b1%a4%7b%2c%71%fa%db%e1%4b%90%75%ff%c4%15%60%85%89%10" | openssl x509 | sudo tee /etc/pki/ca-trust/source/blacklist/DST-Root-CA-X3.pem
sudo update-ca-trust
Check the operation of the services with which access problems occurred.
OpenSSL 1.0.x
- If the system uses an outdated version of OpenSSL, then you must remove the obsolete one from the trusted root certificates as follows: For Debian / Ubuntu edit the file /etc/ca-certificates.conf by setting the symbol ! at the beginning of the line mozilla/DST_Root_CA_X3.crt and run the command:
update-ca-certificates
Server-side.
On the server side there's not much you can do. If you use certificates from Let's Encrypt on your server, you should understand that after 30 Sep 2021 14:01:15 GMT only clients trusting ISRG Root X1 and using Android >= v2.3.6 will be able to connect to your server without problems. At the same time, if clients use OpenSSL, they must use OpenSSL >= 1.1.0 version.
That said, you have a choice - at the cost of dropping support for older Android (leaving Android >= 7.1.1 support), you can retain support for OpenSSL 1.0.x without any client-side manipulation.
To do so, you need to use Let's Encrypt's proposed alternative trust chain for your certificates. This chain excludes DST Root CA X3 and looks like this:
ISRG Root X1 → Let's Encrypt R3 → End User Certificate
To switch to an alternative chain, you need to use the documentation of your ACME client.
If you have have additional questions, you can always contact our support team via ticket system.