Installing Let's Encrypt Wildcard SSL in the Hestia Control Panel
Step-by-step guide to issuing and installing a wildcard certificate.
Let’s Encrypt is a non-profit certificate authority that provides free X.509 certificates for TLS encryption through an automated process designed to replace the complex manual process of creating, verifying, signing, installing, and renewing certificates for secure websites.
Recently, Let’s Encrypt introduced a Wildcard certificate for your domain, allowing you to use SSL without wildcard characters for the domain and multiple subdomains with a single certificate.
This guide works with Linux distributions such as CentOS, Ubuntu, and Debian. The installation example below uses Ubuntu. For CentOS, use the yum package manager instead of apt-get.
Install the acme.sh script:
cd /root
sudo apt-get install socat git
git clone https://github.com/Neilpang/acme.sh.git
cd ./acme.sh
./acme.sh --install
After installation, a cron job will be created to automatically renew your certificate. You can check it with:
crontab -l
Set Let's Encrypt as the default certificate authority:
./acme.sh --set-default-ca --server letsencrypt
Request a certificate:
./acme.sh --issue -d testfrnx.ru -d *.testfrnx.ru --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
Note
Replace testfrnx.ru with your own domain.
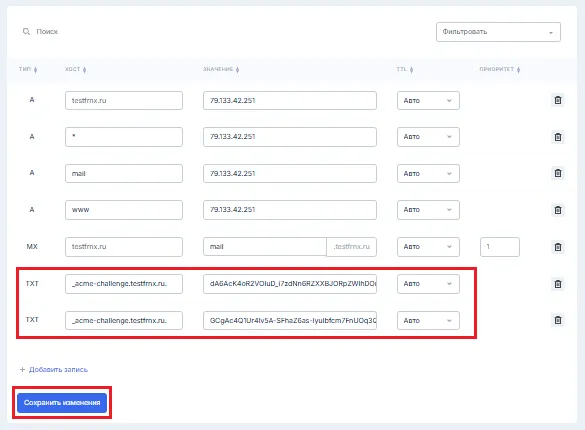
The script will generate 2 TXT records that you need to add in the DNS panel:
[Tue Jun 8 14:23:11 MSK 2021] Domain: '_acme-challenge.testfrnx.ru'
[Tue Jun 8 14:23:11 MSK 2021] TXT value: 'GCgAc4Q1Ur4Iv5A-SFhaZ6as-IyuIbfcm7FnUOq3Qxs'
[Tue Jun 8 14:23:12 MSK 2021] Domain: '_acme-challenge.testfrnx.ru'
[Tue Jun 8 14:23:12 MSK 2021] TXT value: 'dA6AcK4oR2VOIuD_i7zdNn6RZXXBJORpZWlhDOmk96A'
When adding the records, make sure to add a dot at the end of the name, for example:
TXT record _acme-challenge.testfrnx.ru.
value: "dA6AcK4oR2VOIuD_i7zdNn6RZXXBJORpZWlhDOmk96A"
TXT record _acme-challenge.testfrnx.ru.
value: "GCgAc4Q1Ur4Iv5A-SFhaZ6as-IyuIbfcm7FnUOq3Qxs"
Check that the DNS records have updated:
dig txt +short _acme-challenge.testfrnx.ru
"GCgAc4Q1Ur4Iv5A-SFhaZ6as-IyuIbfcm7FnUOq3Qxs"
"dA6AcK4oR2VOIuD_i7zdNn6RZXXBJORpZWlhDOmk96A"
After updating DNS, resume the certificate issuance:
./acme.sh --renew -d testfrnx.ru -d *.testfrnx.ru --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
[Tue Jun 8 15:26:45 MSK 2021] Renew: 'testfrnx.ru'
[Tue Jun 8 15:26:46 MSK 2021] Using CA: https://acme-v02.api.letsencrypt.org/directory
[Tue Jun 8 15:26:46 MSK 2021] Multi domain='DNS:testfrnx.ru,DNS:*.testfrnx.ru'
[Tue Jun 8 15:26:54 MSK 2021] Verify finished, start to sign.
[Tue Jun 8 15:26:55 MSK 2021] Downloading cert.
[Tue Jun 8 15:26:56 MSK 2021] Cert success.
Your certificates will be saved in:
/root/.acme.sh/testfrnx.ru/testfrnx.ru.cer
/root/.acme.sh/testfrnx.ru/testfrnx.ru.key
/root/.acme.sh/testfrnx.ru/ca.cer
/root/.acme.sh/testfrnx.ru/fullchain.cer
Adding certificates to Hestia CP
Note
Hestia CP can be installed by yourself or you can have it set up on our VPS or dedicated servers.
Rename the certificates:
mv /root/.acme.sh/testfrnx.ru_ecc/ca.cer /root/.acme.sh/testfrnx.ru_ecc/testfrnx.ru.ca
mv /root/.acme.sh/testfrnx.ru_ecc/fullchain.cer /root/.acme.sh/testfrnx.ru_ecc/testfrnx.ru.crt
Add the certificates to your domain:
v-add-web-domain-ssl USER testfrnx.ru /root/.acme.sh/testfrnx.ru_ecc/
USER— the user who owns the domaintestfrnx.ru— your domain/root/.acme.sh/testfrnx.ru_ecc/— path to the certificates
Warning
If a certificate was previously added to the domain, update it to the new one:
v-update-web-domain-ssl USER testfrnx.ru /root/.acme.sh/testfrnx.ru_ecc/
Adding a Wildcard SSL certificate for a subdomain
Copy the certificate:
cp /home/USER/conf/web/testfrnx.ru/ssl/testfrnx.ru.ca /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.ca
cp /home/USER/conf/web/testfrnx.ru/ssl/testfrnx.ru.crt /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.crt
cp /home/USER/conf/web/testfrnx.ru/ssl/testfrnx.ru.key /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.key
Add the certificates to the subdomain:
v-add-web-domain-ssl USER sub.testfrnx.ru /home/USER/conf/web/testfrnx.ru/ssl/
Remove temporary files:
rm /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.ca
rm /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.crt
rm /home/USER/conf/web/testfrnx.ru/ssl/sub.testfrnx.ru.key
To update certificates, run this command every 90 days:
./acme.sh --issue -d testfrnx.ru -d *.testfrnx.ru --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please

Set up automatic Let’s Encrypt certificate renewal with Cron by adding this daily job:
0 0 * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null
Note
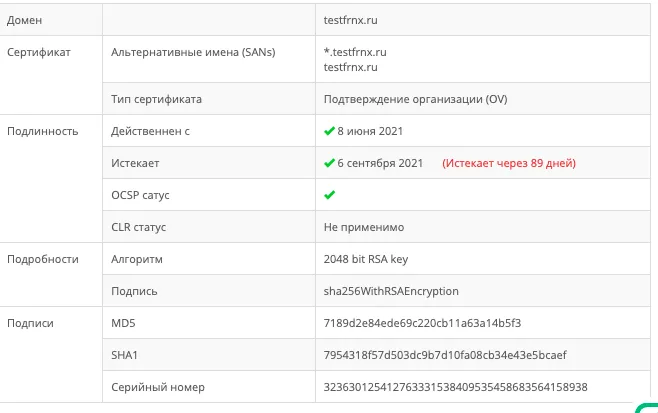
You can check the certificate installation with the SSL checker tool.
Help
If you have any questions or need assistance, please contact us through the ticket system — we're always here to help!