Linux Malware Detect (Maldet) is a scanner that can be used to check the server for suspicious and malicious scripts (shells, spam scripts, etc.) in the system in general or in site files in particular.
The program has a great functionality:
- Find suspicious files;
- Find and quarantine suspicious scripts;
- Find and, if possible, disinfect detected files;
- Scan only those files that appeared and changed during a certain period of time;
- Monitor a certain directory interactively;
- Handle exceptions by adding both specific signatures and paths/specific files on the server;
- Send suspicious files to Maldet servers for analysis;
- Automatically and manually update your own signatures and scanner version;
Installation
Installation is the same for CentOS and Debian:
cd /root
wget http://www.rfxn.com/downloads/maldetect-current.tar.gz
tar -zxvf maldetect-current.tar.gz
cd maldetect-*/
bash install.sh
The install script puts the executable file in /usr/local/maldetect/maldet and makes a symbolic link to it in /usr/local/sbin/maldet. The script also creates the file /usr/lib/libinotifytools.so.0. It creates a daily cron job in /etc/cron.daily/maldet
Use.
Scan only files changed in the last 5 days:
maldet -r / 5
Once the scan is complete, the total number of files scanned, the number of infected files, and the number of cured files will be displayed.
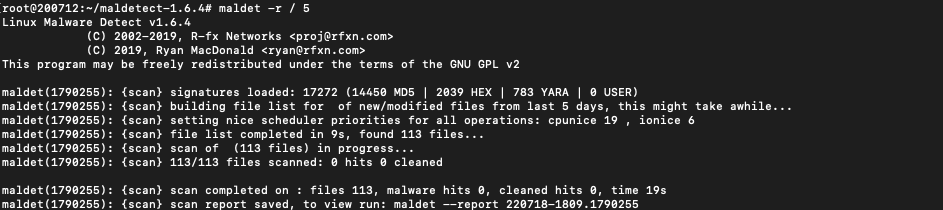
A report number will also be displayed, which can be viewed with a command, e.g:
maldet --report 220718-1809.1790255

Update signature databases:
maldet -u
Move found infected files to quarantine (to /usr/local/maldetect/quarantine):
maldet -q 220718-1809.1890277
Pull files out of quarantine:
maldet -s 220718-1809.1890277
Try to clean up infected files from malicious code inserts:
maldet -n 220718-1809.1890277
Add the malicious code to the maldet signature database:
maldet -c badfile.php
The configuration file maldet is located in /usr/local/maldetect/conf.maldet:
# [ General Options ]
email_alert="1" Turn on notifications from maldet to email. After all, we are conscientious administrators and we keep an eye on what's happening on the server.
email_addr="mail@sysadmin.pm" Specify the mailbox we want to be notified.
email_ignore_clean="0" Receive notifications about cleared files. We'll put 0 here if you want to enable automatic "curing" of the problematic scripts. This question will be dealt with separately.
# [ SCAN OPTIONS ]
scan_max_depth="15" Define the maximum scan depth.
scan_min_filesize="24" Specify the minimum file size.
scan_max_filesize="2048k" Specify the maximum file size the scanner will pay attention to.
scan_clamscan="1" Whether the scanner will use the ClamAV installed on the server.
scan_tmpdir_paths="/tmp /var/tmp /dev/shm /var/fcgi_ipc" The directories for the temporary files that maldet will check.
scan_user_access="0" Whether to allow non-root users to run scans.
scan_ignore_user="" Comma-separated or space-separated users that will be ignored by the scan.
scan_ignore_group="" Groups, comma or space, which will be ignored when scanning.
# [ QUARANTINE OPTIONS ]
quarantine_hits="1" Immediately quarantine any suspicious files found.
quarantine_clean="0" Try to "cure" what is detected. It is up to every administrator to decide whether to enable this option. The author prefers to keep it disabled, with the automatic quarantine enabled and notifications about it.
Daily checking for new files on the server
When installing, maldet creates a file /etc/cron.daily/maldet for the scheduler, if daily checks of new files on the server are not needed, then the file is simply removed, or moved it somewhere else. The file itself already takes into account all paths that are created when working with modern server control panels, usually, modification of this file is not required, only if the administrator needs to add some non-standard path for daily checks.
Running daily, maldet will check for new files on the server, what it finds will be handled according to the settings in the configuration file.
If you have any configuration difficulties or have further questions, you can always contact our support team via ticket system.
