Initial server setup with Ubuntu 16.04
A guide to the initial configuration of the security and usability of your server
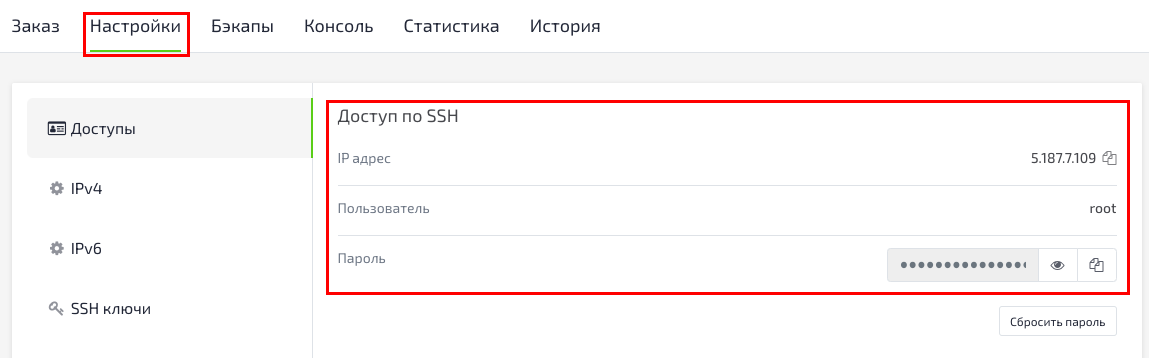
To log into your server, you will need to know the public IP address of the server. You will also need the password for your root user account. You will find the access data in Billing:
To log in, use the command: ``.shell ssh root@IP_address_server
Complete the login process by accepting the host authenticity warning if it occurs and then identifying yourself as a **root** user.
The **root** user is an administrator in a Linux environment and has a very wide set of privileges (rights).
By logging in with a **root user** account you can create a new account which can be used to log in to the server later.
``.shell
adduser username
``.shell
root@kvmde67-19464:~# adduser test
Adding user test' ... Adding new group test' (1001) ...
Adding new user test' (1001) with group test' ...
Creating home directory /home/test' ... Copying files from /etc/skel' ...
Enter new UNIX password
Retype new UNIX password
passwd: password updated successfully
Changing the user information for test
Enter the new value, or press ENTER for the default
Full Name []
Room Number []
Work Phone []
Home Phone []
Other []
Is the information correct? [Y/n] y
After entering the command you will see several questions, the first of which will be the password for the new account.
Enter a strong password and fill in additional information if desired. It is not necessary to enter additional information, you can click **ENTER** in any field you want to skip.
We now have a new account with standard privileges. However, sometimes we may need to perform tasks with administrator privileges.
To avoid having to log out of the normal user account and log in with the root user account, we can set up the option to use something called "super-user" mode, in which our normal account temporarily gets root privileges. This will allow our normal user to execute commands with administrator privileges by adding the word sudo before each command.
From root, run the following command to add your new user to the **sudo** group:
``.shell
usermod -aG sudo account name
Your user with superuser privileges.
Setting up public key authorization for your new user, which will increase the security of your server by requiring a private SSH key to log in.
Creating a key pair: If you don't already have an SSH key pair that consists of a public key and a private key, you need to create one
To create a key pair, run the following command in a terminal on your computer: ``.shell ssh-keygen
Press **ENTER** to accept the address and file name (or enter a different address/file name).
Next, you will be prompted for a passphrase to protect the key. You can enter the passphrase or leave it blank.
Note: If you leave the passphrase blank, you can use your private key for authentication without entering the passphrase
If you specify a passphrase, you need both the private key and the passphrase to log in
Adding a passphrase to the keys is more secure, but both methods have their uses and are more secure than basic password authentication.
This will create a private key **id_rsa** and a public key **id_rsa.pub** in the .ssh subdirectory of the user's localuser home directory
Do not pass the private key to anyone who should not have access to your servers!
After creating the SSH-key pair, you need to copy the public key to your server
If the ssh-copy-id script is installed on your local machine, you can set your public key to any user for whom you know the login and password.
Run the **ssh-copy-id** script with the username and IP address of the server you want to install the key on:
``.shell
ssh-copy-id test@IP_address_your_server
After you enter your password, your public key will be added to the .ssh/authorized_keys file on your server
Now that you can use SSH keys to log into the server, we can further secure the server by disabling password authentication As a result, it will only be possible to access the server via SSH using your public key
To disable password authentication, open the configuration file in a text editor as root or as sudo: ``.shell sudo nano /etc/ssh/sshd_config
Find the line with **PasswordAuthentication**, uncomment it by removing **#** at the beginning of the line, then change the value to **no**:
``.shell
PasswordAuthentication no
In the same file, the other two settings required to disable password authentication already have the correct default settings, do not change these settings if you have not changed this file before:
``.shell PubkeyAuthentication yes ChallengeResponseAuthentication no
After making changes to this file, save and close it (CTRL-X, then Y, then ENTER)
Restart the SSH daemon:
``.shell
sudo systemctl reload sshd
Password authentication is disabled.